
The modern world runs on data, and (re)insurance is no exception. As cyber insurance has matured, the level of data available for (re)insurers has increased accordingly. In previous years, as ransomware appeared, split ransomware and non-ransomware triangles helped insurers demonstrate that ransomware losses often do not develop like data breach claims. The question now is “what data is needed to showcase to the impact of re-underwriting on ransomware?”
Around 2019, cyber insurers began to suffer high loss ratios as ransomware claims increased. It is our impression that this trend increased attritional loss rations 2 or 3-fold, putting most insurers close to or in excess of 100% LR. Which is unsurprising given we believe the frequency of ransomware losses increased nearly 4-fold between 2017 and 2020. In response, cyber insurers were able to obtain impressive rate increases from 2020 to 2022. Now, as the results improve, some expect a sustained rate decrease. The theoretical impact of such a rate change on the performance of a book, assuming all other things are unchanged, is straightforward to model. As the below hypothetical example shows:
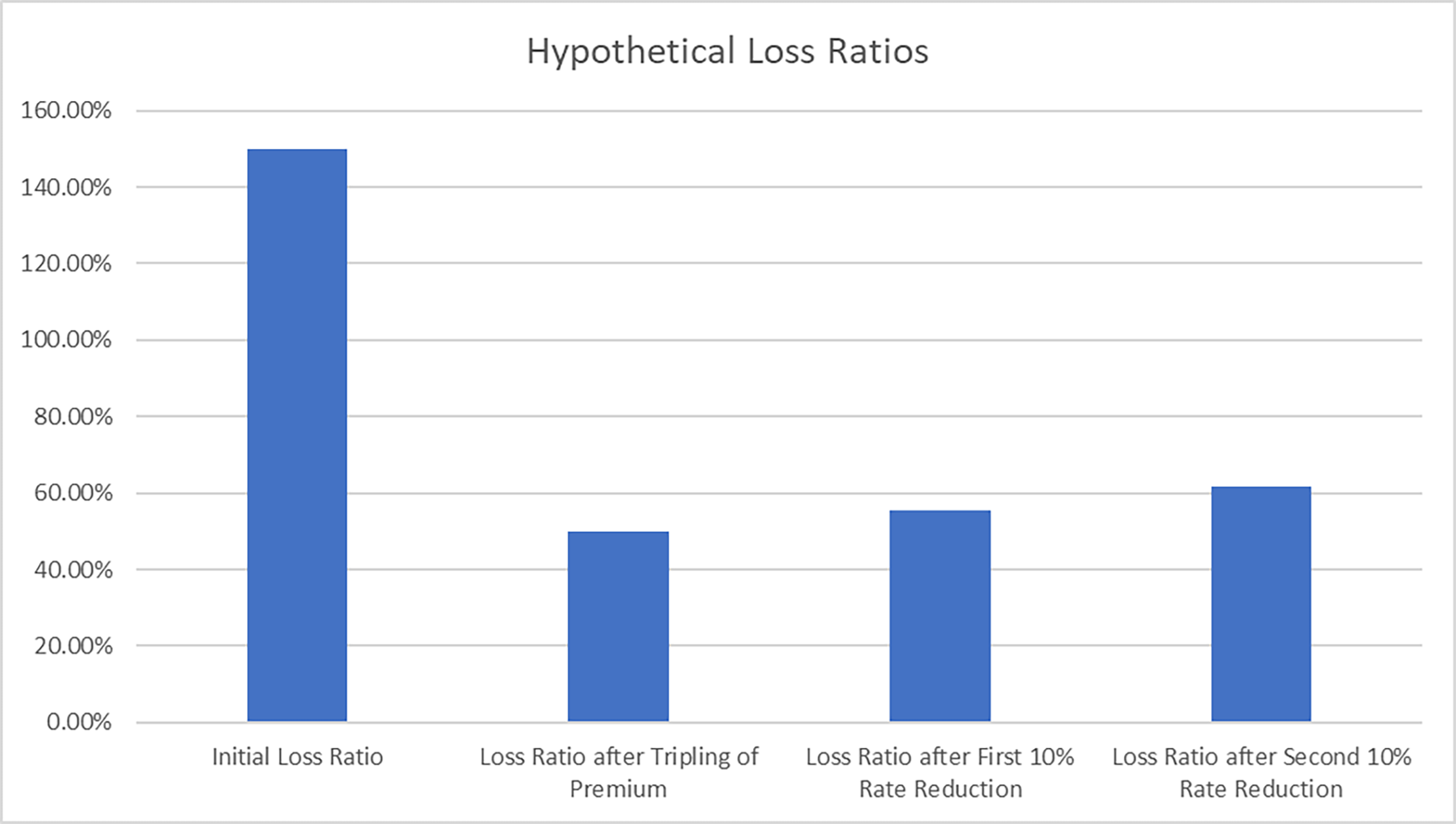
The hypothetical insurer in the example in Figure 1 begins with a worrying 150% loss ratio. But by tripling their rates, they successfully cut their loss ratio to a healthier 50%. Note that this is a hypothetical, and our experience in other lines suggests the full theoretical impact of rate change rarely flows through as quickly as expected. Now, if they give a 10% rate reduction, their loss ratio will rise to 56%. Then, if they give another, all things being equal, it will rise to 62%. And, of course, the insurer also needs to ensure they earn sufficient return to pay for future catastrophe losses, expenses, and their cost of capital in addition to the basic losses. The primary takeaway is that it is notable how the effect of even somewhat modest rate reductions can compound in the loss ratio rather quickly and flow through to the bottom line with similar haste.
It is unclear to what extent the positive results reported for risks written in 2022 stems from rate change, stricter risk selection or a fall in underlying ransomware activity. Or arguably with the lengthening development pattern and returning 3rd party component how positive these results will remain.
It is important to quantify the impact of the re-underwriting actions, as this will help to determine the level of rate adequacy that has been achieved. To date most of the visible improvement is driven by the rate change achieved and the reduction in overall ransomware attack frequency.
By untangling the reduction in claims frequency caused by re-underwriting and that caused by a reduction in attacks due to geo-politics will determine how much is expected to return if geo-politics shift again. By extension how much margin is present in the pricing assuming the world reverts to the mean attack activity over time.
The data required to make this determination in its most basic form would be claim count triangles, which document insured loss frequency over time. As ransomware is a high severity but a relatively smaller portion of all the notifications insurers receive, zooming into just ransomware claims counts will likely provide a much clearer picture. We expect that the actions taken by the market will show significant benefit has been derived from the risk selection improvements, but as an industry we should aim to quantify and improve this as we continue our growth into the 3rd pillar of P&C.
Experts


Related Articles
properties.trackTitle
properties.trackSubtitle

