A guest contribution by our experts Martin Kreuzer and Sigrid Heidenreich in the trade magazine Insurance Day. First published there on August 15, 2025.
Personal insurance policies are becoming increasingly important as they can help safeguard the digital lives of private individuals and their families from online fraud and cyberattacks. Merchants worldwide estimated losses only to online payment fraud at around US$ 44bn in 2024 (Statista). Since numerous insurance companies today offer coverages and affiliated services, it is an essential task for insurers to assess the accumulation potential for this insurance segment. Clarity on accumulation will also support further growth of the private cyber insurance market and enables insurers to further diversify cyber insurance books.
In most past cases, cyberattacks on private individuals were carried out individually. Therefore, historical examples of cyber incidents affecting hundreds of private individuals are rare. Furthermore, the amount of damage in such scenarios always depends on the specific coverage, the services included, and the development of penetration rates. It should also be borne in mind that, with the help of AI, cyberattacks that were previously carried out individually could potentially be replaced or exacerbated by automated attacks, which means that the probability of cumulative events in cyber insurance for private customers could increase.
With a view to advancing the understanding of insurers and reinsurers about the accumulation potential in personal lines coverage, Munich Re has drawn on the judgment of its internal cyber experts: Taking into account events that are typically covered by personal lines cyber policies, they have identified possible scenarios and classified them in terms of their accumulation potential.
The diagram below shows the relevance and criticality of single coverage elements in respect of susceptibility to accumulation events:
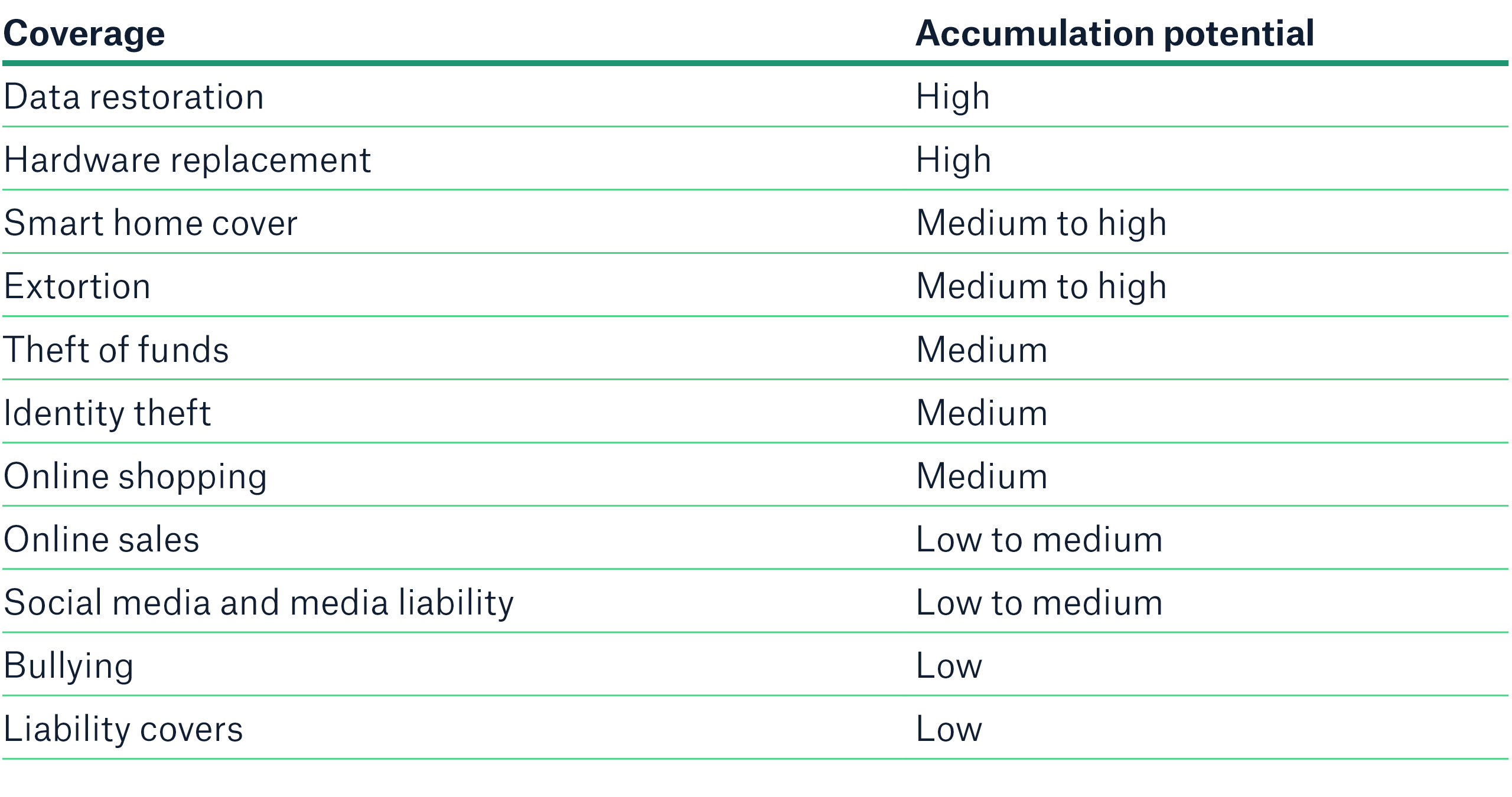
The seven most critical scenarios – experts’ assessment:
- Data restoration / malware decontamination
Today, there are approximately 7.2 billion smartphone connections worldwide, which, according to DataReportal’s “Global Digital Insights”, represent about 87% of total mobile devices. The heavy usage of smart devices leads to increased attack surfaces for individuals. It has never been easier for cybercriminals and other threat actors to spread malware on smartphones and other personal devices. Especially since AI may identify exploits at an accelerated rate or create new strains of malware to spread them on a large scale in an automated way, not only companies but also more and more private individuals are likely to become victims. A widespread malware event that renders data inaccessible and compromises thousands of devices will be covered under data restoration/malware decontamination and thus seems to be one of the most likely accumulation scenarios at present. It is therefore assessed as a coverage rated as having a “high” accumulation potential.
- Hardware replacement
The line of reasoning for this coverage is similar to that outlined above. Whereas physical damage to computing devices caused by a mass malware attack on personal devices seems unlikely, experts see a significant potential for insurers to choose hardware replacement as the most cost-effective option for covering data/system restoration, which may accumulate to a substantial loss amount. The accumulation potential of this coverage is therefore also assessed as “high”.
- Smart home cover
Given the interconnectedness and the widespread usage of the same hardware and software components in many electronic devices, and due to logic similarities to the two scenarios above, the accumulation loss potential for smart home devices is evident. A mass malware attack could cause system restoration costs (including hardware replacement, if that is more cost-effective) for all smart home devices, e.g., security systems, cameras, smart appliances, or home entertainment systems. In addition, such an attack could also involve ransom demands (see next paragraph). The bandwidth of existing devices, software, or operating systems is very wide. Whether a device is impacted usually depends on the type, brand, and components of the respective device typically covered. Experts at Munich Re therefore assess the accumulation potential of this coverage as “medium to high”.
- Extortion
In their private lives, individuals very often lack a stronger sense for cyber hygiene[1]. Therefore, picking “low-hanging fruit” could become increasingly lucrative for cybercriminals. Since the amounts extorted from private individuals have tended to be rather small in reality, hackers may feel incentivized to launch attacks on a larger scale by targeting hundreds of private persons at the very same occasion. As AI not only is expected to enable automated distribution of malware but also facilitates cryptocurrency transfers, AI raises concerns that the risk for ransomware attacks on private individuals might increase in the future. These developments also make accumulation scenarios around extortion more likely. Experts assess the accumulation potential of extortion coverage as “medium to high”.
- Theft of funds
Major threat scenarios are expected to initially involve large-scale phishing campaigns, which might enable attackers to target multiple victims simultaneously. In this context, the targets would be larger banks and their private customers. With this kind of a “distribution channel”, the potential for accumulation is obvious. Since banking liability generally is strong in many regions (e.g., in which banks bear the burden of proof of unauthorized transactions), in many cases the bank would need to reimburse damages to their clients as a result of unauthorized transactions.
- Identity theft
A large-scale data breach at a single target may lead to a spike in identity theft claims, as stolen credentials and a large repository of personal identifiable information might appear in the dark web for further exploitation. If those details contain financial or health-related information, they may become even more attractive to criminals than less critical data elements. Criminals can then use this stolen data to open fraudulent accounts, file false claims, or gain access to government benefits. Against the backdrop of numerous data breaches affecting nearly all industries, ranging from hotel chains to financial institutions to the healthcare sector, identity theft cases have surged over the past years and are likely to continue to increase in the future. Experts at Munich Re assess the accumulation potential of identity theft coverage as “medium”.
- Online shopping and sales
To date, fraudulent activities related to online sales and shopping are the largest loss drivers within the claims book of personal cyber insurance companies. Usually, these events are individual cases only, but professional and automated phishing campaigns that direct online shoppers to fake shops are on the rise, and so is the affiliated accumulation potential. In the future, AI agents may be able to perform social engineering and manipulate humans on a large scale. If malicious AI agents were able to intervene in transactions – for instance, between buyers and sellers – scenarios involving mass fraud might emerge in that context.
Accumulation scenarios are manageable
The potential for large accumulation losses for insurers heavily depends on the composition of their portfolios (e.g., ratio of commercial to personal lines cyber business). From Munich Re’s perspective, only malware scenarios would also trigger losses in the personal lines cyber insurance cover as well as the commercial policies. As indicated by experts’ judgment, these losses would derive from the coverages of data restoration and of hardware replacement and, to a certain extent, also from extortion and smart home cover. These findings should be reflected in insurers’ malware accumulation models. Incidents such as WannaCry and NotPetya have already demonstrated in the past how fundamental it is to take accumulation scenarios into account when building cyber-portfolios. In addition, AI will be making previously individually targeted attacks within personal lines cyber more prone to automation and accumulation.
Overall, Munich Re considers accumulation in personal lines to be manageable from the perspective of primary insurers and reinsurers. Expanding the cyber portfolio might even help further diversify the cyber book. Munich Re will continue working on its own accumulation scenarios constantly and sharing learnings with clients and the cyber market. This is also an important contribution to deliberately grow this important segment of business to protect private life against the threats of our digital world.
Market development: Joint efforts needed
Contact


Related solutions
properties.trackTitle
properties.trackSubtitle