
Munich Re’s
Data Risk Intelligence
Don’t cut back on data and IT security – but on the effort involved!
properties.trackTitle
properties.trackSubtitle
With the Data Risk Intelligence solution you can significantly reduce the time and expense involved in implementing the GDPR and at the same time improve the quality of your operations
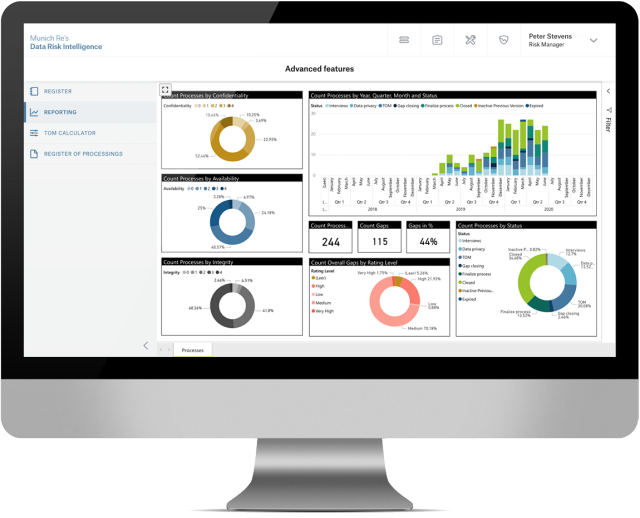

Reduce your risks with the easy-to-use analysis and workflow tool
Munich Re’s Data Risk Intelligence enables you to considerably simplify and accelerate your data and information protection processes, and at the same time provides you with an analysis that gives you a comprehensive overview not only of the current status of your data and information protection but also your IT risk management.
You will even receive this individual analysis automatically in the form of comprehensive documentation in accordance with regulatory requirements, as well as individual recommendations for action to reduce your risks to the greatest possible extent. And all this in only 3 steps.
And all this in only 3 steps.
To maximum data protection in just 3 steps
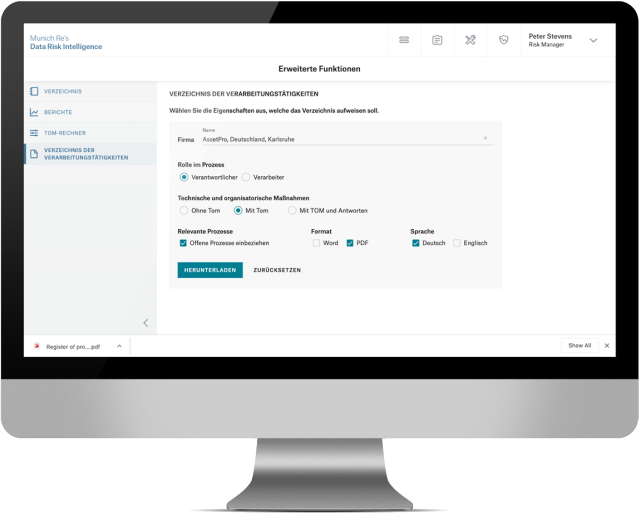
- A decision-based catalogue of questions for the analysis of personal and nonpersonal data
- Structured, individual user guidance through the entire question process
- Collaboration throughout by assigning specific “roles”
- Checking and processing of crosscompany and cross-country data flows
- Evaluation of the criticality, integrity and availability of data on the basis of the findings of the catalogue of questions
- Deduction of legal conclusions as well as appropriate technical and organisational measures (TOMs)
- GDPR-compliant data protection
- Identification of IT compliance deficiencies and IT security vulnerabilities (GAPS)
- Management of relevant data processing and data privacy information at one place
- Audit logging of risk manager approval and management board decisions
- Generation of documents in different formats and versions (with or without TOMs)
- Document management – for more extensive documents, too
Security is good. Eightfold security is even better!
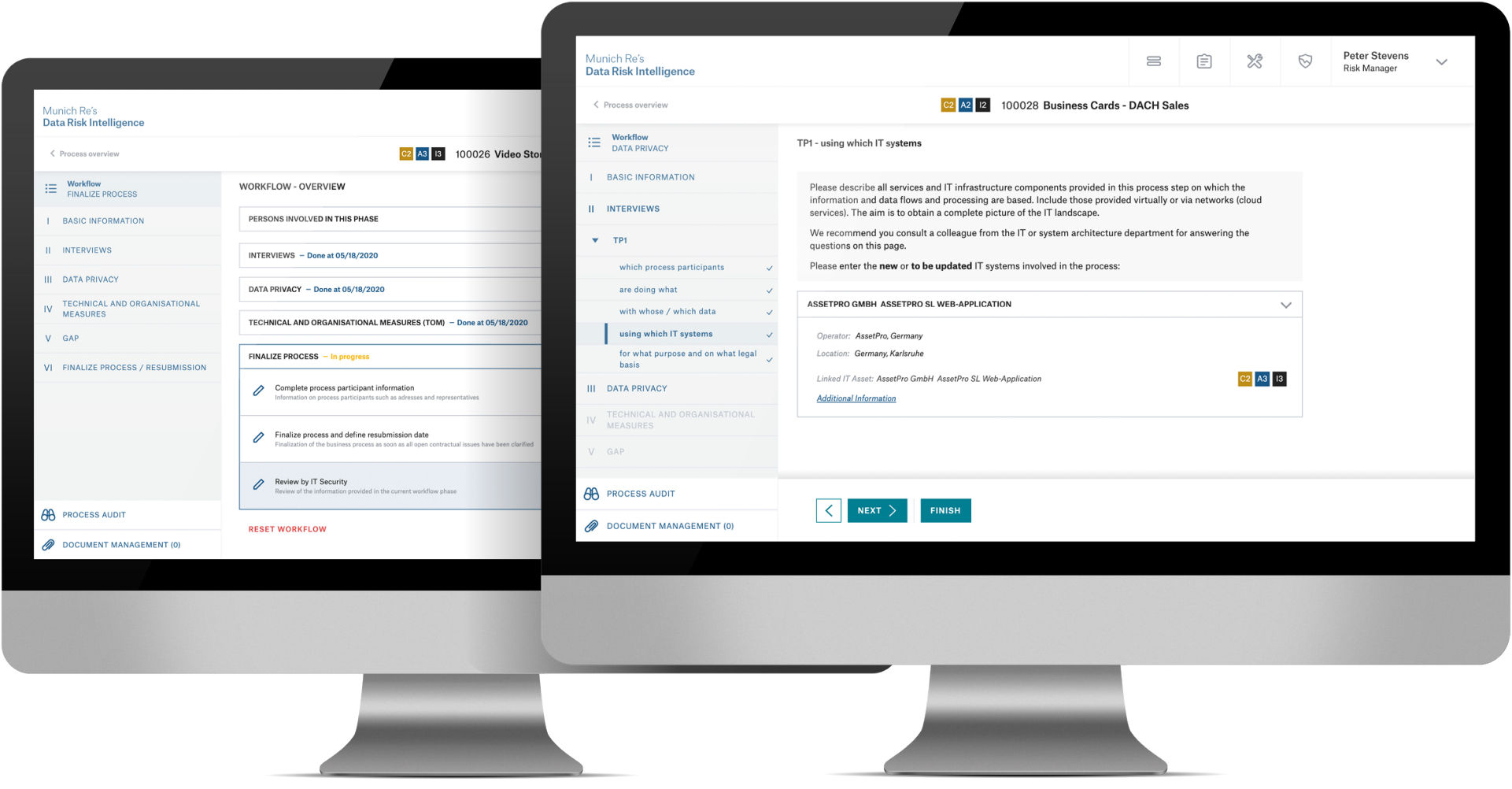
1. Data protection management
- Situation analysis using a predefined, workflow-based interview catalogue
- Data protection organisation based on interdepartmental cooperation
- Automated creation of required documents
- Logging and visualisation based on comprehensive reporting
- Flexible and customer-specific adaptation through administration functions
2. IT risk management
- Classification and assignment of data
- Evaluation of technical and organisational measures
- Identification of information security and IT security vulnerabilities, so that these can be dealt with subsequently
- Check on third parties involved in the process by identifying relevant controls
3. Protection of business secrets
- Evaluation of processes without personal data, but with critical and sensitive data (e.g. contracts or blueprints)
- Identification of criticality, i.e. the confidentiality, integrity and availability of the data types defined for this purpose
- Identification of vulnerabilities based on specific controls defined for this purpose
4. Cybersecurity assessment
- Creation of a checklist for cybersecurity requirements
- Review on the basis of a TOM list extended by information security checks
- Extended documentation and handling of vulnerabilities through involvement and escalation of various stakeholders
- Identification and management of vulnerabilities and the resulting risks (advanced risk assessment)
5. Tech. and org. measures
- Preconfigured and customisable customer-specific TOMs and checks
- Continuous checking and adjustment of stored TOMs
- Automatic documentation of the corresponding results and optimisation measures
- TOM calculator for fast and specific generation of technical and organisational measures for specific process characteristics
6. Third-party risk assessment
- A workflow-supported check on all third parties involved in the process from a data protection and IT risk management point of view
- Integration of third parties through “identity and access management”
- Determination of individual TOMs for external parties
- Central administration of all service-specific information and documents
7. Compliance management
- Assessment of third parties on the basis of specific relevant monitoring requirements
- Identification of risks for all parties involved in a business process
- Management of the identified vulnerabilities
- Continuous review of the checklist of controls and appropriate adjustments based on identified vulnerabilities
- Audit functions per process as well as across-the-board by the role (auditor)
8. Analysis of vulnerabilities
- Carrying out a risk assessment on the basis of checks revealing non-compliance
- Definition of mitigating measures
- Integration of experts on risk acceptance through delegation and escalation to different stakeholders (e.g. CISO, management etc.)
- Use of automatic risk management on the basis of ISO 31000 (advanced risk assessment)
Select the edition that best suits your requirements. And simply extend it whenever you wish
Thanks to its modular structure you can not only adapt the solution to the individual maturity level of your integrated data protection and IT risk management, but further modules can also be flexibly added to the editions “Enterprise” and “Professional” at any time.
The Data Risk Intelligence Platform
All editions are based on the common Data Risk Intelligence platform. It forms the technical basis and provides the common user interface for all modules – including all those you book at a later date. This means you always have an overview and can operate in your familiar environment.
Standard Data Risks Module
This module groups together all the standard functions of the Data Risk Intelligence solution. From process analysis via risk assessment to documentation (see list on the right for the complete range of functions). Together with the Data Risk Intelligence platform this module forms the Professional Edition.
Enterprise Data Risks Module
In order to optimally integrate the solution into your company’s application landscape, simply choose the Enterprise Edition – this already includes the Enterprise Data Risks module and therefore not only ensures full group capability but also provides an additional comprehensive TOM list.
Data Breach Module
This optional module enables you to document data protection violations through initial and follow-up reports, to assess the obligation to report them, and to store them under an incident number for further processing in the system. Also available as stand-alone Data Breach Edition (see list on the right).
Additional modules
You can also cover more extensive regulatory requirements with the optional expansion modules, which can be seamlessly integrated into the solution.
- Data Subject Rights Module: Offers you the structural documentation and management of enquiries from data subjects.
- Advanced Risk Assessment Module: Replaces the Basic Risk Assessment vulnerability analysis in the workflow and thus offers the possibility of extending the scope of the analysis and adapting it to
| Enterprise Edition | Professional Edition | Data Breach Edition | |
| Data Risk Intelligence Platform | included | included | included |
| Standard Data Risks Module | included | included | optional¹ |
| − Rights and roles concept | ● | ● | ○ |
| − Customisable workflow with interview | ● | ● | ○ |
| − Register of processing activities | ● | ● | ○ |
| − Data protection impact assessment | ● | ● | ○ |
| − Automatic document generation | ● | ● | ○ |
| − Management dashboards (PowerBI) | ● | ● | ○ |
| − Multilingual expansion option | ● | ● | ○ |
| − GAP analysis and monitoring | ● | ● | ○ |
| Enterprise Data Risks Module | included | optional¹ | optional¹ |
| − Integration in the application environment | ● | ○ | ○ |
| − Group capability | ● | ○ | ○ |
| − Comprehensive TOM list | ● | ○ | ○ |
| Data Breach Module | optional¹ | optional¹ | included |
| Additional modules | |||
| Data Subject Rights Module | optional¹ | optional¹ | optional¹ |
| Advanced Risk Assessment Module | optional¹ | optional¹ | optional¹ |
| Learn more |
○ Available as soon as the corresponding module is purchased
¹ Can be purchased additionally at any time
All the benefits at a glance
Get it all. For more detailed information just download our brochure “Data Risk Intelligence” for free!
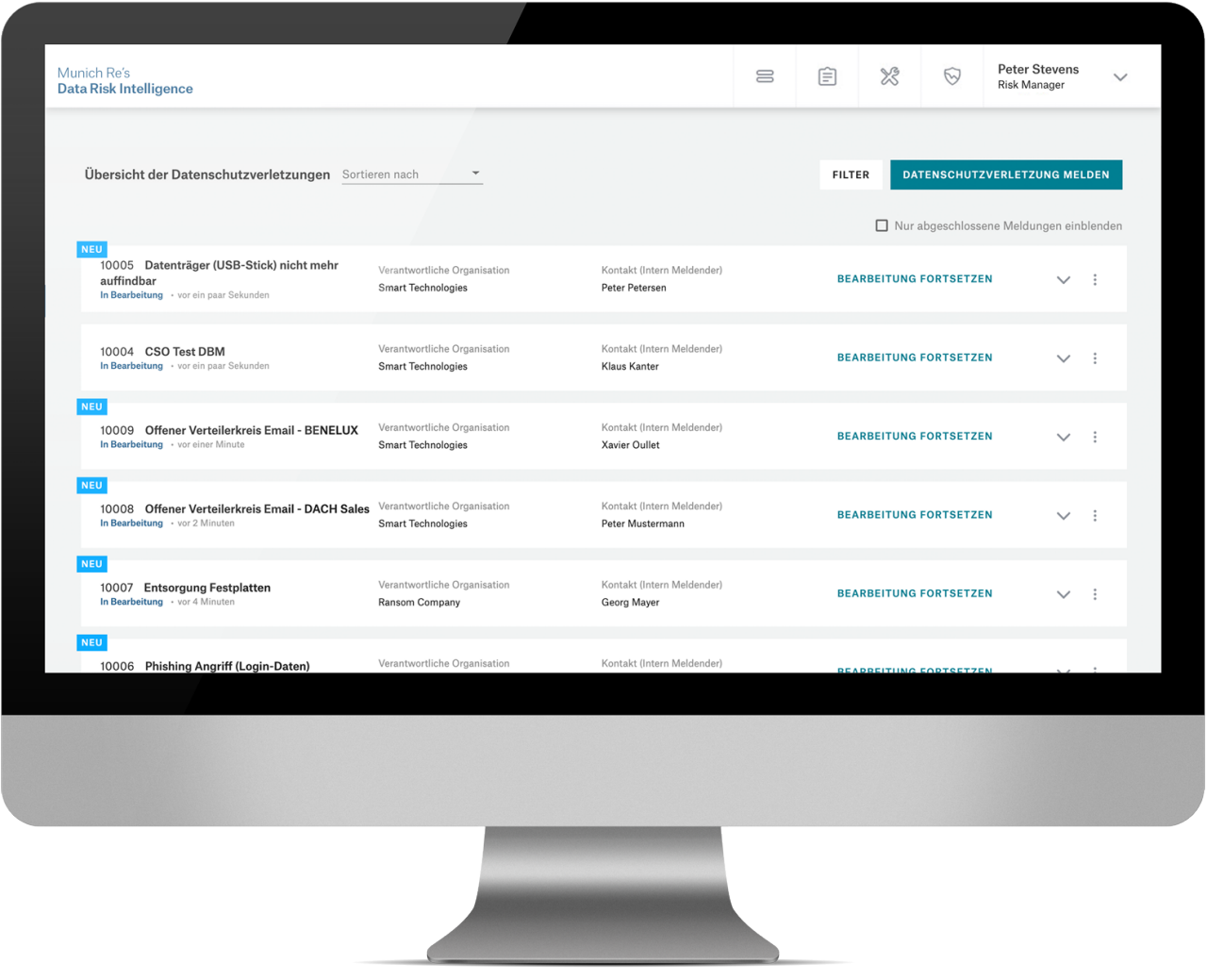
Data breaches can be highly expensive. Unless you act in line with GDPR thanks to Munich Re‘s Data Breach Edition
Data Breach Edition enables you to document data breaches and assess the obligation to report them. The entries can be supplemented over time and reference numbers can be stored in the system for further processing. Learn more …
How about trying our solution right now? Or would you rather talk to someone in person?
We believe you can never have too many good partners. You are a Value Added Reseller, Managed Service Provider or System Integrator and would like to include our solutions in your portfolio? Then simply apply for our Risk Suite Partner Programme.
/Nicole_Schmitzberger.jpg/_jcr_content/renditions/original.image_file.640.640.file/Nicole_Schmitzberger.jpg)




